Entra ID in M.App Enterprise

What is Entra ID?
Microsoft Entra ID (formerly Azure Active Directory) is Microsoft's cloud-based identity and access management service that provides centralized authentication, authorization, and user management capabilities for organizations. It serves as the backbone for securing access to Microsoft 365, Azure services, and thousands of third-party SaaS applications through protocols like SAML, OAuth 2.0, and OpenID Connect. The platform offers features including single sign-on (SSO), multi-factor authentication (MFA), conditional access policies based on risk assessment, privileged identity management, and comprehensive identity governance tools. Built on a globally distributed infrastructure, Entra ID integrates seamlessly with on-premises Active Directory through Azure AD Connect for hybrid identity scenarios, supports modern authentication methods like passwordless sign-in and certificate-based authentication, and provides extensive APIs and PowerShell modules for programmatic management and automation of identity operations at enterprise scale.How to use Entra ID in M.App Enterprise?
When creating aNew Tenant you are offered several possibilities to authenticate the user for your Apps page. One of them is called Entra ID and if you want to use it, you have to define different parameters in order to get it up and running:
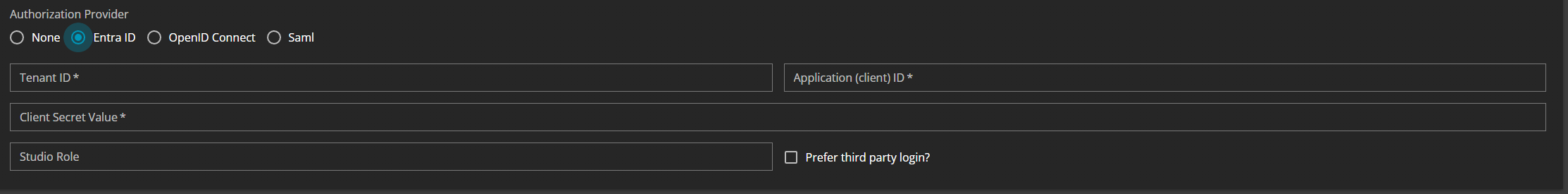
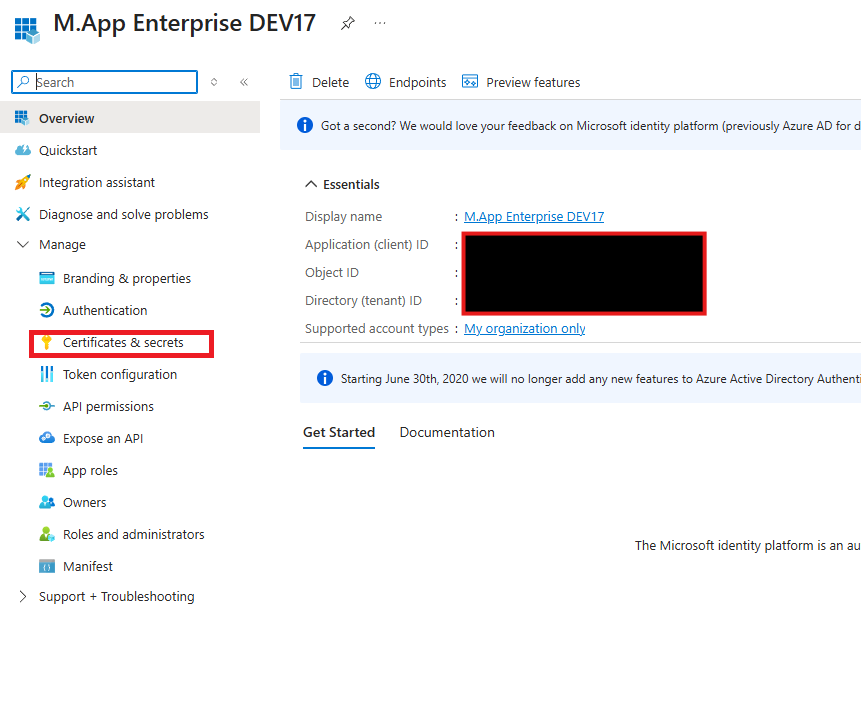
Tenant ID:You will get the information on the start page of your applicationApplication (client) ID:You will get the information on the start page of your applicationClient Secret Value:You can create the secret ID atCertificates & Secrets
Studio Role: Users are normally allowed to authorize themselves into a tenant’s Apps context with the third-party authorization protocol.Studio Roleis a shared setting between all third-party authorization protocols which allows a tenant’s Studio context to be authorized with the selected protocol too, if the authorized user has a role value corresponding to the value specified in this field. In the case of Entra ID, the Identity Provider should insert this value with the keyroleorgroupas a key-value pair in the returned authorization token.Prefer third party login:If you want to prefer the Entra ID login over the on-premise login defined in the tenant
Parameters needed in Entra ID portal?
We have to set some parameters in the Entra ID portal as well likeRedirect URIs and API permissions. Let's get over them step by step:
Redirect URIs: Can be found atAuthentication
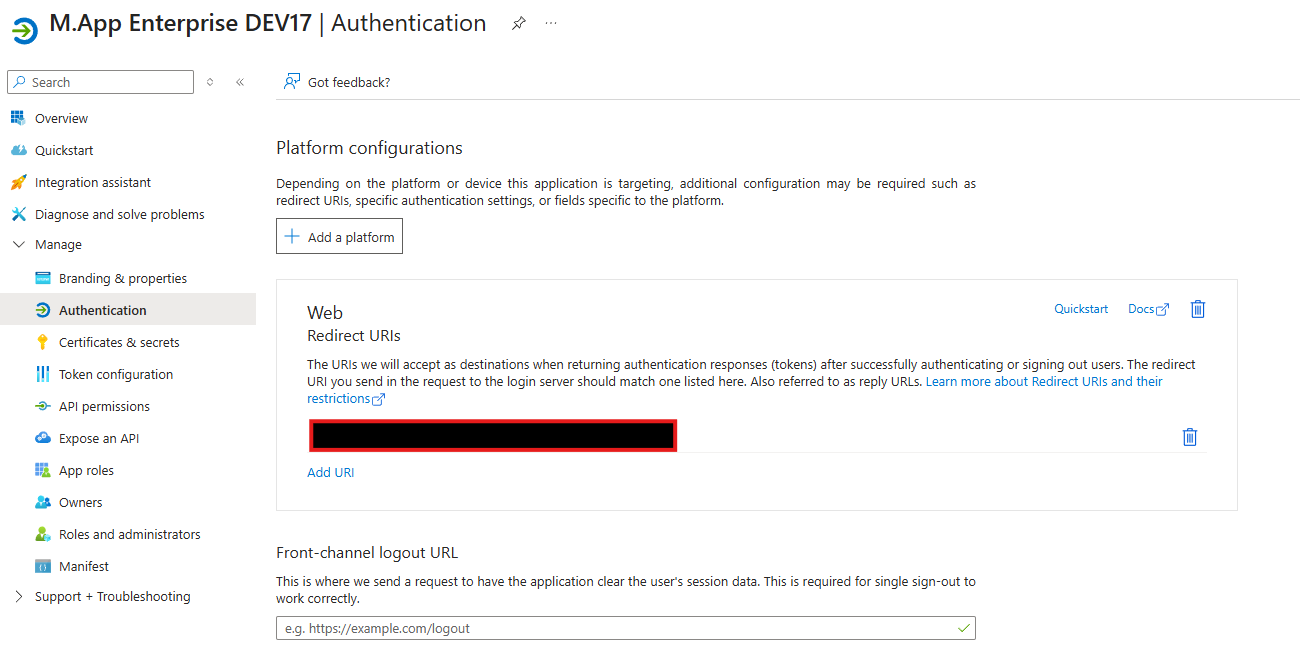
⚠️
Redirect URIs must be with
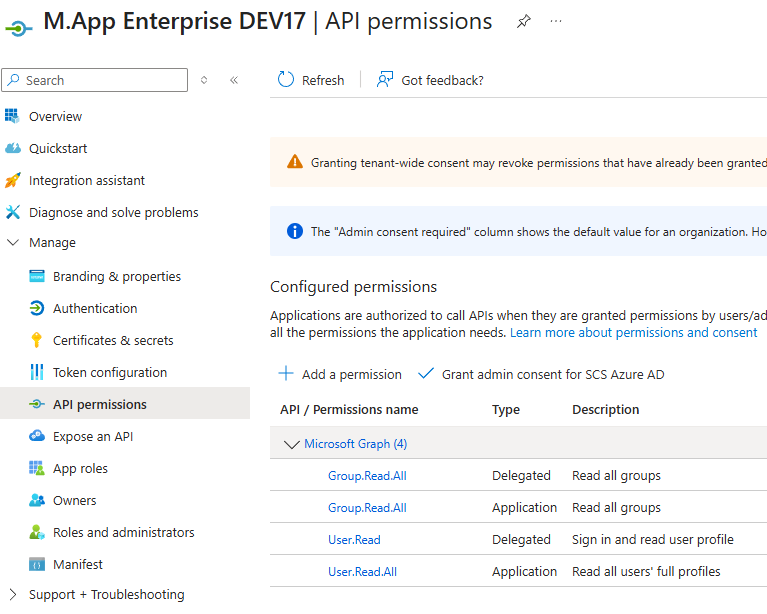
https://. This only works if you open up MAE Studio or Apps page with https://API permissions: Can be found atAPI permissions
You only want the Apps user be authenticated with Entra ID
User.Readper default already activated with Microsoft GraphGroup.Read.All (Delegated)that is the only way offered from Microsoft to get the names of the groups. With that names we can check whichclaims & rightsare set for this user on a group level
You want the groups be syncronized within M.App Enterprise Studio with Entra ID
Additionally to:User.ReadGroup.Read.All (Delegated)
User.Read.All (Application)Group.Read.All (Application)
💡
If you want to use groups = claims within M.App Enterprise e.g. layer visibility, ActionSet visibility and so on